A message from our founder:
2024 has been a great year for us at Unredacted, growing in many ways that we didn’t even imagine were so quickly possible. We set out to explore whether becoming a 501(c)(3) non-profit was feasible. We ended up putting in the research and work to do it, and we formally incorporated as Unredacted Inc in May and received our 501(c)(3) determination letter from the IRS in June. We received a huge amount of support, from kind words to donations, and even a grant from the Human Rights Foundation. All of the support we’ve received has inspired us and allows us to continue our growth.
2025 will surely be a difficult and challenging year for the fight against Internet censorship, and the fight for everyone’s right to privacy. Access to free and open information is as extremely important as it ever was. With some level of critical thinking, the truth can be found. We’re refocusing and doubling down on our mission to fight Internet censorship and protect people’s privacy by building out more censorship-resistant and privacy-friendly Internet infrastructure and services, while polishing the existing.
So much has already happened, so read on to see in full detail what we accomplished in 2024.
Zach
Executive Director
Unredacted Inc
A year in review (2024)
General Updates:
Initiatives:
Censorship Evasion (CE):
Secure Infrastructure (SI):
Conclusion:
Website
This year, we put a lot of work into the content and design of our website. The front page was redesigned, we added breadcrumbs on nearly all pages for easier navigation, and redesigned our donation page. Furthermore, we added new pages and content such as our transparency report, Supporters page and launched Unredacted Updates, where you can get a summary of what we’ve worked on each month. Transparency is important to us, and there will be more to come in 2025.
Want to read more about the inner-workings our projects & services? Check out our blog!
Hardware
Unredacted has largely operated on a mix of dedicated hardware that we rent from various hosting providers. Unfortunately one of those providers, Hetzner, mysteriously cancelled our account at the end of October. We’ve since migrated to more reliable providers. However, important infrastructure such as our Tor exit relays, XMPP.is, and Unredacted Matrix server run on top of rented dedicated servers still. This past year, we’ve pursued purchasing and colocating hardware that we fully own. So far, we’ve built out redundant edge routers, aggregation switches and a PoE switch (seen below) which will power a special project that we’re working on. We won’t give any hints on what the PoE powered Raspberry Pis are for now, but we’ll be announcing how and why we built them in early 2025. What we’ll say is that they’re scalable, efficient and more affordable to operate in the long run.


We’re also in the process of building an high-availability virtualization cluster with Ceph for storage too. That hardware is still in testing, but we plan to fully deploy it in early 2025 as well. The new cluster will power XMPP.is, the Unredacted Matrix server and various other new services that we’ll spin up in 2025.
The hardware purchases that we made wouldn’t have been possible without the amazing support and donations we’ve received from our community. We’d especially like to thank the Human Rights Foundation for providing a grant to us.
Network

For a long time, we have operated our own network on top of one of our hosting providers. Recently, we became an ARIN member and received our own ASN (Autonomous System Number), AS401401 – which, in HTTP status codes means “Unauthorized.” ARIN must have thought we were cool. 🙂

We also received IPv6 and IPv4 prefixes, which we’ve started advertising to our upstream providers. Our edge network at the time of writing consists of 18 virtual machines across various hosting providers for diversity and redundancy. We built this network for the special project mentioned above in the hardware section, and in 2025 we’ll write about how and why we built it on our blog.
Operation Envoy: Defeating Censors

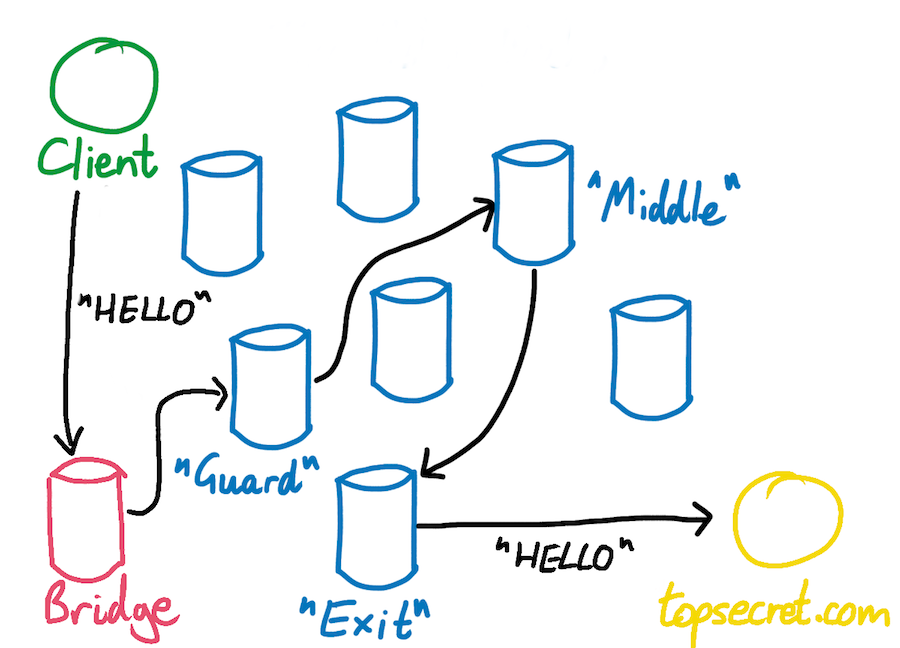
In July of 2023, we started Operation Envoy, an initiative that consists of ‘envoys’ which help to deliver messages (packets) to and from the Tor network. This helps users experiencing Internet censorship, or those who wish to mask their use of Tor. Previously, we focused heavily on deploying Tor snowflake proxies around the world.
This year, Operation Envoy had its 1st year anniversary. We thought a lot about Operation Envoy’s future, and we decided that it should consist of more than just Tor bridges. Operation Envoy now consists of everything we operate that helps people reach the free and open Internet, or particular services such as Signal & Telegram.
Operation Envoy includes:
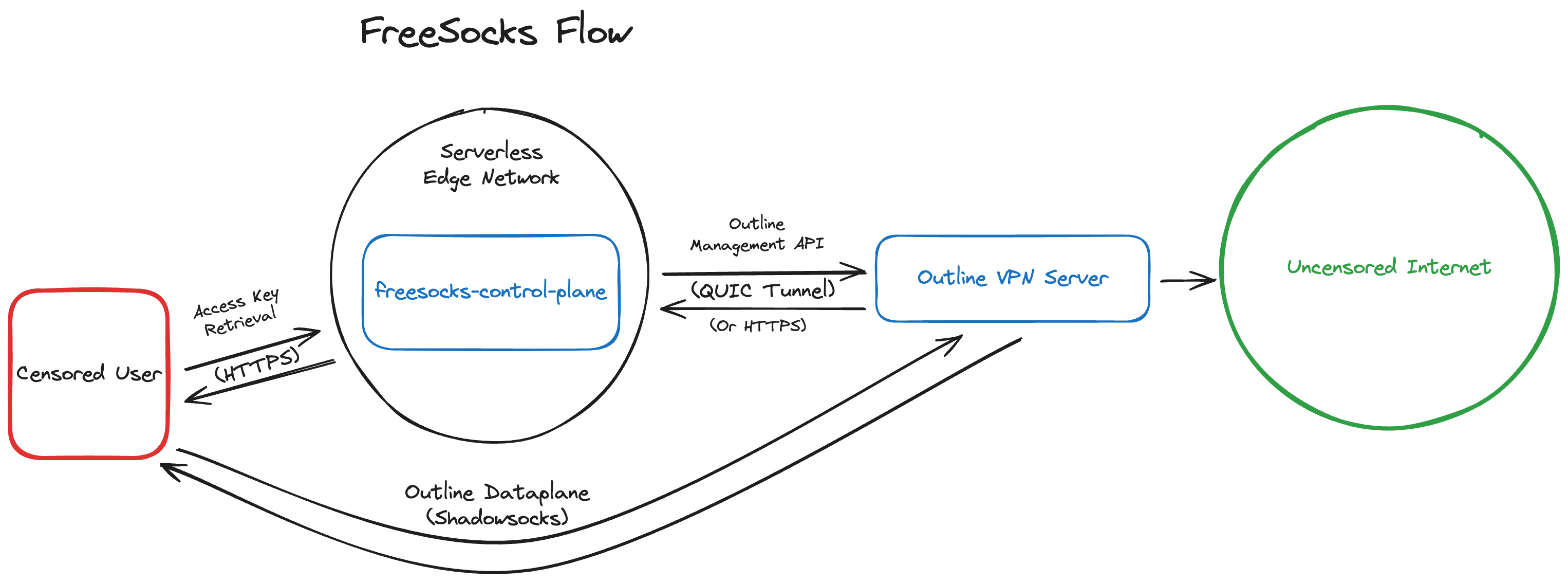
- FreeSocks (currently uses Outline, which is based on Shadowsocks)
- Unredacted Proxies (uses Signal’s TLS proxy & Telegram’s MTProto proxy)
- Unredacted Tor bridges & snowflake proxies (using WebTunnel, meek or snowflake)
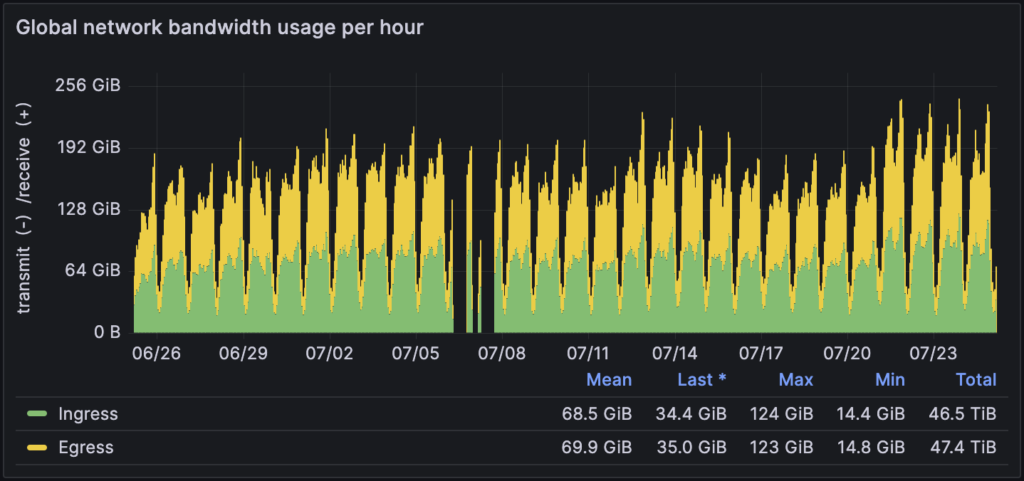
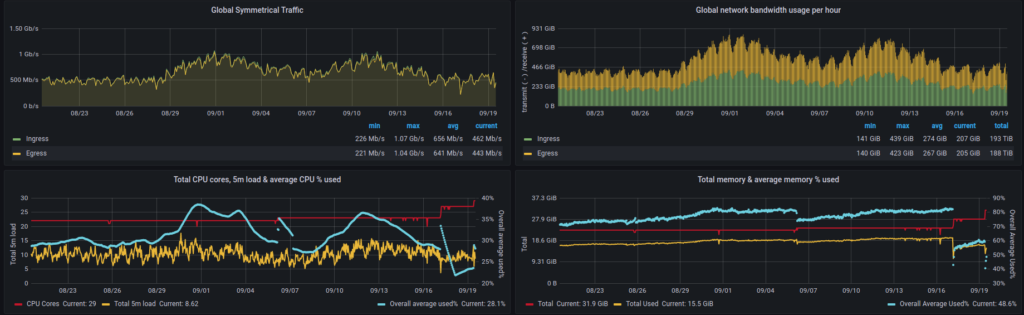
Around the same time last year, we had served around 121TiB of traffic in a single 30 day period. As of December of 2024, in the last 30 days we’ve served over 192TiB of traffic to across all Operation Envoy services, which is a significant increase, but also due to the reclassification of what an ‘envoy’ is to us.

If we continue to average at this new rate of bandwidth over a year, that would be over 2.2PiB!
Last year, we ended with 31 CPU cores and 53GiB of RAM. Looking at CPU core and RAM counts now, we ended the year with 91 cores and 106GiB of RAM, which is again a significant increase – but also due to the reclassification.

Our anonymized & aggregated Operation Envoy metrics are publicly accessible, and you can see the direct impact that we’re making.
In 2025, we will continue expanding our CPU core and RAM counts, but we can’t do it without your help! If you like what we do and want to support our mission, consider making a donation.
FreeSocks, proxies that circumvent censorship

FreeSocks, our service that provides free, open & uncensored Outline (Shadowsocks) proxies to people in countries experiencing a high level of Internet censorship was open sourced in June. It also hit its first year of existence in December of 2024, and has expanded rapidly.
Since its launch, FreeSocks has issued over 10,000 access keys to people looking to circumvent Internet censorship. This is an amazing milestone, and we’re happy to be helping so many people across the world. We’ve received a lot of positive feedback, and it has inspired us to continue our work on the service.

In 2025, we’ll be continuing our work on a full rewrite of the freesocks-control-plane (FCP), the code which powers FreeSocks and allows for access keys to be issued, and have their state tracked. The rewrite will convert the existing code from JavaScript to TypeScript, and feature an API + web control panel which will allow us and others to manage their FCP deployment much more easily.


We’re also planning to potentially move away from Outline’s server software, and utilize raw Shadowsocks, Vmess, VLESS and Trojan proxies to offer more options to our users. To note, existing access keys and Outline’s client will still work with raw Shadowsocks.
We can’t run free & awesome services like this without your help.
Tor exit relays

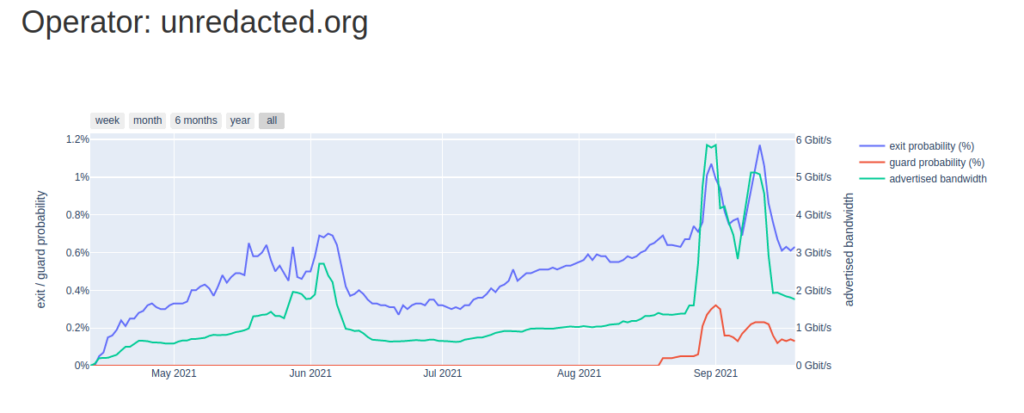
In our efforts to help people evade censorship, and protect their right to privacy, we have operated numerous high-bandwidth Tor exit relays since 2021.
We’re currently #20 in the top exit families, and have a 0.55% exit probability according to OrNetStats. That means your connection through Tor may be one of the 0.55% which exits traffic through our relays.

Currently, we have around 5Gb/s of throughput capacity (3Gb/s more since last year), however in practice this has been lackluster due to hosting provider network congestion and rate-limits. With our new hardware, we’re planning to migrate all of our Tor exit relays to our colocation in early 2025, which should allow for better throughput and control.

Regardless, over the past 30 days we have received and transmitted over 366TiB of bandwidth. If this rate continued for a year, that would still be over 4.2PiB of bandwidth usage for a whole year, quite an achievement.

With your help, we can do even more, and continue to push a lot of traffic for the Tor network.
Unredacted Proxies

In 2024, we quietly announced Unredacted Proxies – which allow people to connect to messaging services such as Signal and Telegram, without exposing the fact to their ISP or government.

Unredacted Proxies are a part of Operation Envoy, and are quite useful to many people around the world where Signal & Telegram are blocked. We’ve had a lot of good feedback about the service, and while we don’t directly count the amount of users – we can see that it’s being utilized by many when looking at bandwidth metrics. We’ve particularly seen great interest from people in Russia and Iran.
For those interested in the technical side, we use Signal’s TLS Proxy and Telegram’s MTProto for our proxies.
Chat services
Our oldest projects are our chat services. XMPP.is was launched in 2015 and our Matrix server was launched in 2021. For many years, thousands of individuals have used our chat servers to exchange messages back and forth between friends and family. These remain a crucial part of our mission, as it allows people to communicate securely and privately. We regularly maintain and update these services, but there’s nothing notable to announce for them this year.
If you want to chat with us and other like-minded people, why not join one of our communities?

Funding
Las year, we struggled with funding. However, this year has been amazing in terms of funding. We received a record amount of donations, and even received a grant from the Human Rights Foundation! We’re eternally grateful to our community and supporters, and we promise to always use your money effectively. To date, no one at Unredacted makes any money for the work they do, and we intend to keep it this way until we are fully sustainable.
2024 EoY Balance Totals (USD):
- Cryptocurrency balances (calculated at time of writing): $35,681
- Bank balance (at the time of writing): $246
Total: $35,927
2024 Grant Totals (USD):
- Human Rights Foundation: $5,000
Total: $5,000
We expect that with our current expense and growth rate, these funds will allow us to smoothly operate for at least 2-3 years. To continue our mission, and rapidly expand, we’ll need your support! We have many very ambitious and interesting work & projects in 2025.
If you want to support us, we allow one-time or recurring donations via multiple payment methods, including PayPal, credit cards, cryptocurrency (including XMR & ZEC), Open Collective, Patreon & Liberapay.

In 2025, we plan to be much more transparent in terms of our spending and funding.
What’s next?
In 2025, we have a lot of work ahead of us. We’ll be building out new infrastructure, creating new services and revamping existing ones. We’re expanding at a rapid pace, and we’re going to continue doing so. The fight against Internet censorship and for people’s right to privacy will be especially important in the coming year.
Happy holidays!
Sincerely,
The Unredacted Team