
In July of last year (2023) we launched Operation Envoy, our effort to deliver packets to and from the Tor network which helps defeat Internet censorship. This is achieved by Unredacted operating Tor bridges, also known as Pluggable Transports. Tor bridges obfuscate (bridge) the connection a user makes when connecting to Tor so that it looks like any normal connection and disguises the fact that they are connecting to the Tor network. Each Pluggable Transport has its own unique way of obfuscating the connection, such as WebTunnel which mimics HTTPS traffic, one of the most common types of traffic on the Internet.
What a connection to the Tor network looks like with a bridge in the path
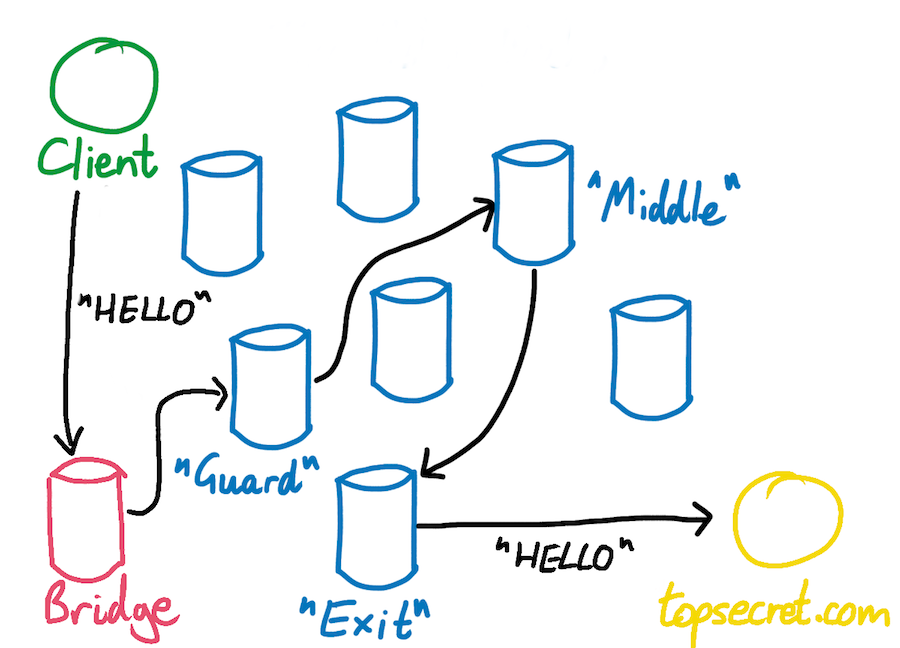
Historically, and for a long time we’ve focused our efforts on deploying dedicated snowflake proxies around the world in strategic locations close to Internet users that face a high level of Internet censorship in their countries. Today, we’ve added a WebTunnel and meek bridge into the mix. Adding more Tor bridge types means that users have more ways to connect to the Tor network in the event that one protocol / obfuscation technique gets blocked.
Our meek bridge

To deploy our meek bridge, we worked with the team at Tor after volunteering to run a new bridge. Due to how meek works with Tor, there is some setup on their end as well because they use a technique called domain fronting. This is a technique to disguise a connection and route it through popular, and more painful to block CDN networks like Microsoft Azure. Meek bridges remain a crucial method to connect to the Tor network in several countries.
To see our new meek bridge statistics, you can click here.
Our WebTunnel bridge

As described earlier in the post, WebTunnel is a bridge type which mimics HTTPS traffic, one of the most common types of traffic on the Internet. It’s based on HTTPT which resists active probing attacks that censors use to block censorship circumvention techniques. WebTunnel will likely, and ultimately become a very important bridge type for Tor as it rolls out and gains popularity due to the protocol it disguises itself as and its resistance to active probing.
Our new WebTunnel bridge uses a unique configuration that we came up with to hide the IP of the bridge behind a TCP proxy service. This allows us to easily switch the ‘front’ of the WebTunnel bridge in case its IP gets blocked. In the future, we plan to write about how we did this once we’ve confirmed its stability over time.
To see our new WebTunnel bridge statistics, you can click here.
Current Operation Envoy stats
As it stands today, we have a collective of virtual machines consisting of 31 CPU cores, 40GB of RAM and multi-gigabit unmetered links dedicated to serving Tor bridge traffic across the world.

On an average day, we are pushing almost 2TB of symmetrical bandwidth per day. That’s almost 60TB per month!

We can’t make all of this possible without your help. If you like what we do, please consider making a donation. As time goes on, and with more funding we’ll continue to expand our Operation Envoy footprint by deploying more Tor bridges across the world. Your help can make a real impact for Internet censorship circumvention.